Boost your cybersecurity using Blockchain and AI

Even the largest companies have been at the receiving end of cyberattacks. As new business models evolve and businesses adopt technologies to automate processes and “go digital”, hackers too come up with new ways to exploit vulnerabilities. Depending on the nature of business and the attackers’ objectives, customer data, personally identifiable information, intellectual property related information have all been targeted with the intention of stealing data for use illegally. The fear of illegal hacking has become so all-pervasive that there is now serious concern that even the outcomes of political processes such as elections can be illegally influenced. Infecting enterprise systems with ransomware has also been on the rise; such attacks prevent users from accessing their systems till the “ransom” is paid- usually in the form of cryptocurrencies such as Bitcoins.
The above risks exist despite the use of enterprise-grade firewalls, anti-virus software, network security measures as well as periodic vulnerability assessments and penetration testing.
Enhancing productivity
At one level, information security policies are being redesigned to comply with the “triad model” that focuses on Confidentiality, Integrity and Availability. This so-called “CIA triad model” is applied to both Application and Network aspects of an enterprise.
- Confidentiality: Measures are put in place to ensure that only authorized people can access information, and that the “wrong people” cannot get to it.
- Integrity: Pertains to steps taken to prevent any unauthorized changes to data while in transit and indeed, during its lifecyle.
- Availability: Related to timely availability of information for use through proper maintenance of hardware, ensuring adequate communication bandwidth, providing failover, redundancies and Disaster recovery Plans.
At another level, newer technologies such as Blockchain are being integrated and supplemented with Artificial Intelligence (AI) to build more robust and trustable systems that significantly reduce the risk of cybersecurity breaches.
How does the Blockchain-AI combination enhance security?
Blockchain technology allows data in digital format to be held in a Distributed Ledger shared across millions of computers. Anyone with access to the internet and wishing to participate in the public blockchain network can access the data. This is referred to as a public blockchain, where the data is public but verifiable. On the other hand, private blockchains are permission-based platforms generally established for one or more specific business entities (companies a group of firms, or divisions within an organization). In both types of blockchain, because data is not stored in any one location, it cannot be tampered with. Data is reconciled continuously, so unauthorized changes cannot be made.
To understand blockchains in action, consider a musician who is skeptical about publishing music on the internet due to concerns around plagiarism. Blockchain technology allows the artiste to create a backup that contains pieces of digital music or other materials that can be copyrighted. Once the backup is complete, a certificate with cryptographic evidence is issued to defend the copyright against infringement. The record of the original music pieces and their creation dates are recorded in the blockchain, allowing for confirmation that a piece of music existed at a certain time in the past and was authored by that particular artist. Every transaction is consummated only when the required members of that blockchain network validate the transaction. It is important to note that each member is identified by their digital identity, and not actual identity.
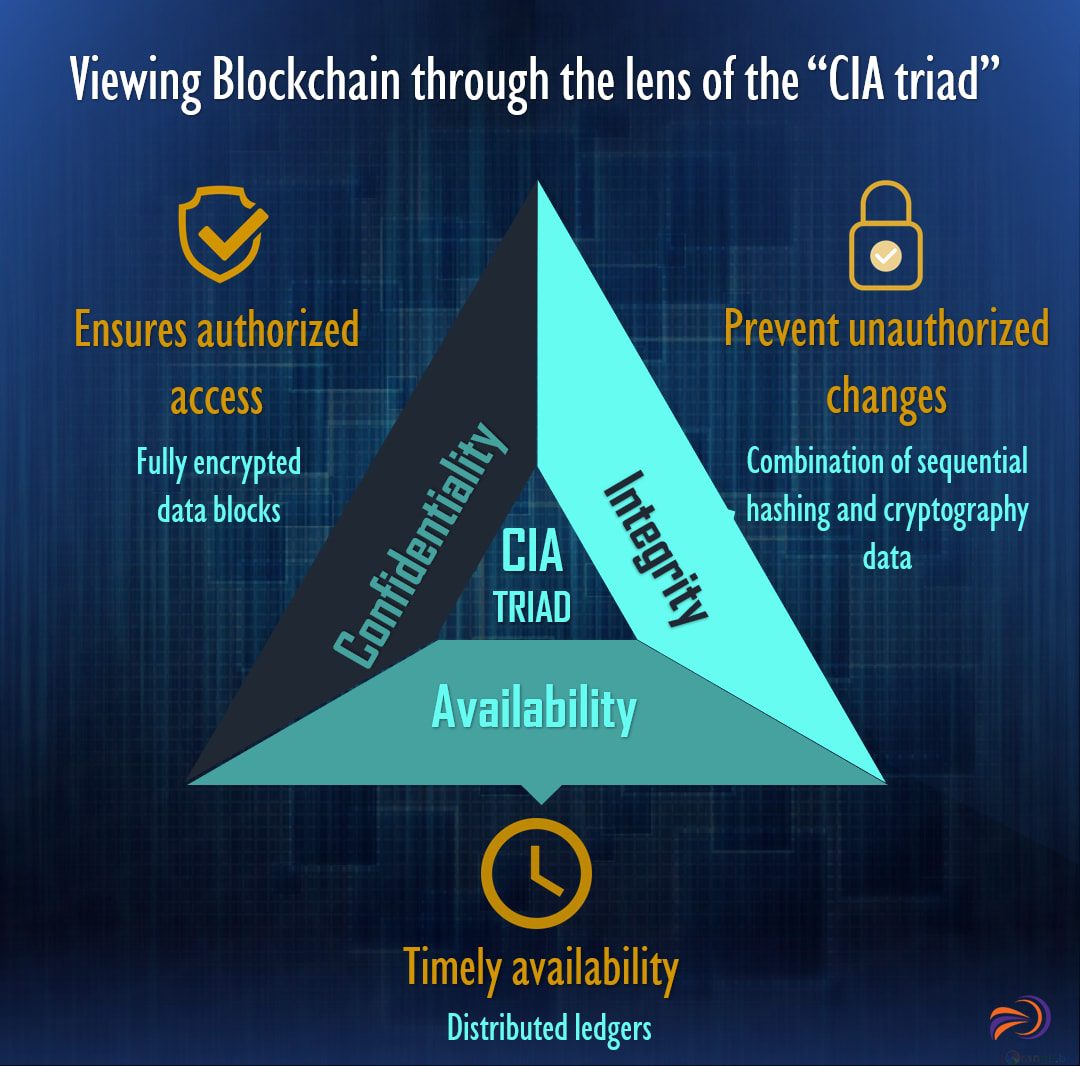
Viewing blockchain through the lens of the “CIA triad” reveals why this technology has definite advantages from security and privacy perspectives.
At another level, newer technologies such as Blockchain are being integrated and supplemented with Artificial Intelligence (AI) to build more robust and trustable systems that significantly reduce the risk of cybersecurity breaches.
- Confidentiality: Even if an attacker gains access to a blockchain network and the data, it does not mean that s/he can read or retrieve the information. Data blocks can be fully encrypted, thus guaranteeing confidentiality.
- Integrity:Transactions processed using blockchain technology are highly trustable because of the combination of sequential hashing and cryptography data stored in distributed ledgers are tamper-proof when compared to a conventional database
- Availability:Distributed ledgers mean blockchains do not have a single point of failure. This decreases the chances of an IP-based attack disrupting normal operations (e.g. DDoS).
s with other more conventional technologies, blockchain implementations and roll-outs too must be supported by appropriate system and network cyber security protocols and controls, due diligence, practice and procedures. It is important to keep in mind that blockchain technology, though superior, does not provide a universal panacea for all cybersecurity ills. During the DevCon 2 event in Shanghai a DDoS attack exploiting a vulnerability in the Go-based Ethereum client’s smart contract implementation prevented miners from mining further blocks. Smart contracts in the DAO, a decentralized organization built on top of Ethereum, were attacked. The attacker exploited a bug in the smart contracts, leading to a theft of 60M Ether (http://www.coindesk.com/dao-attacked-code-issue-leads-60-million-ether-theft/).
Also, not all information is amenable to the use of blockchains. In a brownfield implementation where on-chain and off-chain information are stitched together AI becomes a powerful ally to blockchain technology, supplementing supervision where direct human observation or monitoring is not possible. Through pattern recognition and advanced algorithms, AI can guarantee verifiable and manageable data, thereby enhancing trust within the given systems.
Conclusion
No information system or cyber defence can be regarded as 100 % secure. In one of the security incidents, Bitcoin investor sues AT&T for $224 Million after mobile-linked theft (https://www.ccn.com/bitcoin-investor-sues-att-for-224-million-after-mobile-linked-theft/). Even what is deemed safe today may not remain so tomorrow given the ingenuity and technical sophistication criminals use to constantly identify and develop new methods of attack because of the lucrative nature of cybercrime. Compared with conventional systems certain inherent capabilities of blockchains provide higher levels of data confidentiality, integrity and availability. Even so, just like with design, deployment and management of other systems, organizations using blockchains must also adopt cyber security protocols, controls and standards within their technical infrastructure and incorporate Artificial Intelligence to monitor, control and protect themselves from cyberattacks. This is easy to overlook when blockchain based systems co-exist with systems based on more conventional database designs.